For openwrt devices exposed directly to the internet such as in a DMZ and need to have ssh access without compromising too much, we will have to follow these steps to achieve some basic security. Internet traffic is very much infested with bots trying to brute force into systems so this is a small but very useful step to harden your security and privacy. The main idea is to disable password authentication and use only a certificate with a custom ssh port.
First is to create a public and private key pair in the client from which we usually perform administrative tasks then we follow by copying the public key to our openwrt device. We continue by changing the standard ssh port 22 for a non standard port preferably in the range of dynamic or Private Ports (49152-65535) and we finish by creating a config file in .shh to manage the settings to log in with the certificate generated at the beginning and disabling password authentication.
In your local device (from where you intent to access your openwrt) generate the certificates. Go to your users .ssh directory (/home/[your_local_user]/.ssh) and type:
ssh-keygen -t ed25519 -a 100 -f .ssh/key-openwrtThis will generate key-openwrt (private) and key-openwrt.pub files. We will create a config file later to configure and use the connection for convenience.
Now its time to copy your public key to openwrt:
ssh-copy-id -i key-openwrt.pub root@ip_addressAs you are trying to copy the pub key as root, the key will be associated to the root user. You will be prompted to provide your root password once. If the copy is successful lets try to log in without the password. The private key in your local machine will get verified against the public key you’ve just copied over to openwrt and if validation is successful you will log in as your openwrt’s root user.
ssh -i key-opewrt root@server_ip If login was successful we can now create a config file (named config) inside the .ssh directory. This file will manage your key based authentications but before doing that, let’s change the default port to put the new info in your config file:
Log in in the LUCI portal and click in Administration –> ssh-access:
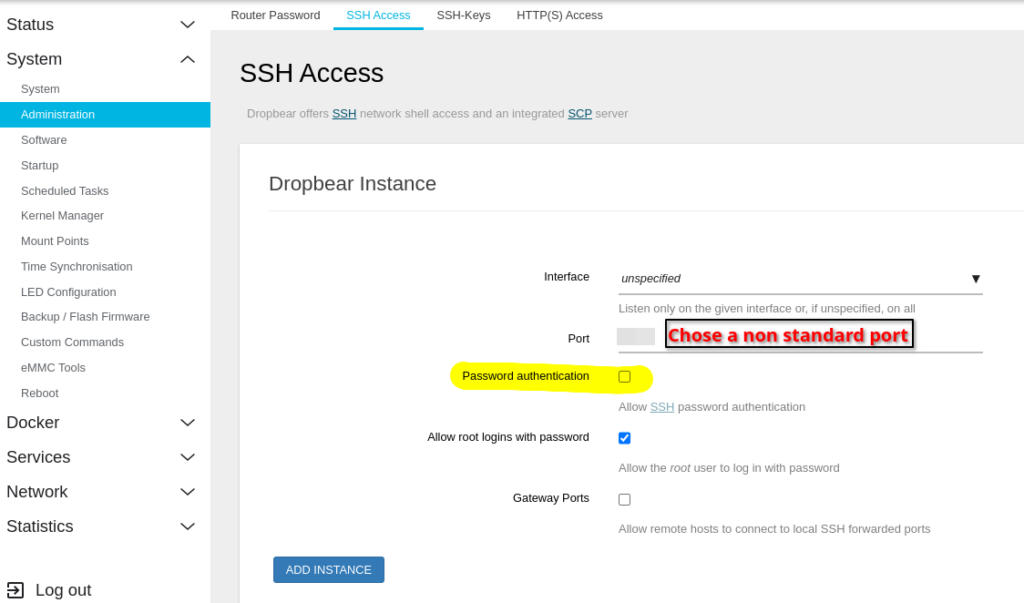
Choose a non standard port for ssh and disable password authentication. Save and exit. Now lets create the config file in /home/[you_local_user]/.ssh:
nano config
host openwrt
Hostname [ip_address]
User root
port [example:49595]
PreferredAuthentications publickey
IdentityFile /home/[your_local_user]/.ssh/key-openwrtOnce the files has been saved and if everything went well you should be to log in without a password using your key pair. Try out the configuration:
ssh openwrtDone!

